As crypto adoption accelerates, so does the need for secure, flexible ways to manage digital assets. Two popular technologies – Multisignature (Multisig) and Multi-Party Computation (MPC) – are often brought up when discussing wallet security and access control. But what do they actually mean? How do they work? And which one is right for your business?
If you’re not deeply technical, don’t worry – in this post, we’ll break down the difference using simple analogies, visuals, and practical examples.
A Vault Full of Gold
Let’s start with a relatable analogy.
Imagine you and a few partners store gold in a high-security vault. To prevent fraud or theft, you don’t want any one person to open the vault alone. You need a system of shared control.
There are two ways to set this up:
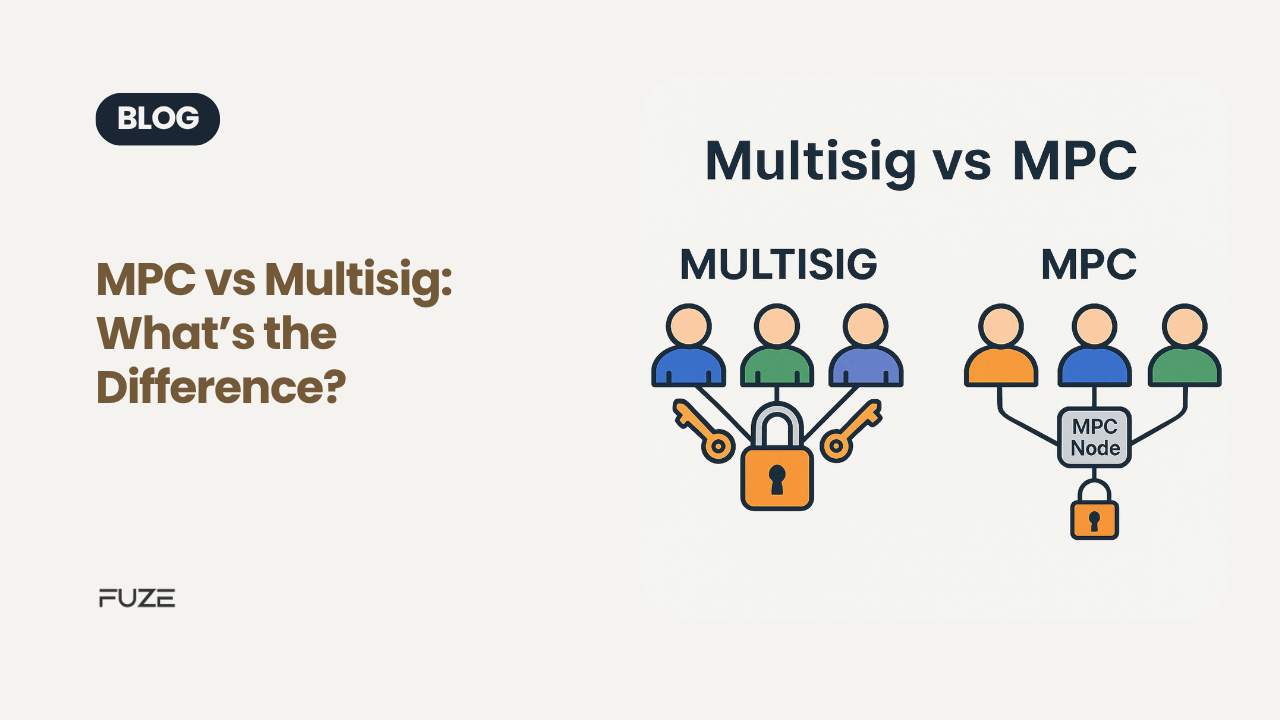
Option 1: Multisig (Multisignature): Like putting multiple locks on the vault
-
The vault has 5 locks.
-
Each of your 5 partners has a unique key.
-
You configure the vault to require at least 3 of those 5 keys to open it.
This is how Multisig works on blockchains like Bitcoin or Ethereum (via smart contracts). It’s a rules-based setup, where a minimum number of authorized parties must individually approve a transaction.
Pros:
-
Simple and battle-tested.
-
Transparent – everyone can see on the blockchain that multiple approvals were required.
-
Useful for shared wallets (e.g., company treasuries, DAOs).
Cons:
-
Limited flexibility – changing participants or rules requires on-chain updates.
-
Privacy is poor – the multisig setup and signers are visible to everyone.
-
Implementation differs across blockchains – not all chains support the same features.
Option 2: MPC (Multi-Party Computation): Like sharing pieces of a single secret key – invisible cooperation
Now imagine:
-
The vault has just one lock.
-
But instead of giving the full key to one person, you split it into secret pieces.
-
Each person holds a piece, and when needed, they work together to generate a valid key without ever assembling it in one place.
That’s MPC in action – it uses advanced cryptography so that multiple parties can collaboratively “sign” a transaction, without revealing or reconstructing the private key.
From the outside, it looks like just one person signed – even though multiple people participated behind the scenes.
Pros:
-
Chain-agnostic – works on any blockchain that supports regular signatures (e.g., Bitcoin, Ethereum, Solana).
-
Private – no one knows multiple parties were involved.
-
Flexible – easy to rotate participants, revoke access, or add devices.
-
Great for mobile wallets, institutions, and any system needing seamless security.
Cons:
-
Complex to implement – requires sophisticated infrastructure.
-
Harder to audit – no visible “multi-party” footprint on-chain.
-
Often depends on off-chain coordination or vendors.
Why the Confusion?
MPC and Multisig both aim to reduce single points of failure – meaning, they protect against the risk of one person or device being compromised. But they do so in very different ways.
Multisig is visible and rule-based, great for open accountability.
MPC is invisible and cryptographic, perfect for security with minimal friction.
You’ll often see them compared, debated, or even combined in some enterprise-grade solutions.
Architectural Differences
Multisig Wallet Architecture
-
Each participant holds a full key.
-
Wallet logic is enforced on-chain (Bitcoin script, Ethereum contract).
-
Transactions show multiple signers.